Todas las sesiones de AnyDesk están protegidas mediante TLS 1.2 con cifrado AEAD.
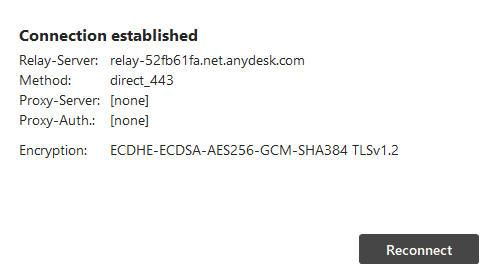
Puede ver el tipo de conexión, el modo de cifrado forzado, el estado de verificación del cliente y la huella digital haciendo clic  en la barra de herramientas.
en la barra de herramientas.
Funciones de seguridad en el cliente de AnyDesk
AnyDesk proporciona varias funciones de seguridad para ayudarlo a proteger su entorno:
Configuración de cliente personalizada : configure directivas de seguridad en el cliente personalizado. Para obtener más información, consulte Custom AnyDesk client.
Acceso desatendido exclusivo : acceda al dispositivo remoto solo utilizando la contraseña desatendida.
Hash de contraseña salado: las contraseñas se almacenan de forma segura mediante tokens hash salados.
Autenticación de dos factores : proteja el acceso desatendido habilitando two-factor authentication.
Lista de control de acceso (ACL)
Puede restringir las sesiones entrantes mediante el Access Control List para permitir solo identificadores o alias autorizados.
Solución local
Para entornos de alta seguridad, AnyDesk ofrece una opción de implementación On-Premises . Esta versión funciona independientemente de Internet, lo que le brinda un control total sobre sus datos.
Baja de antiguos empleados
Si un empleado que usa AnyDesk deja su organización, siga los siguientes pasos para proteger su entorno:
Eliminar su cliente
Si conoce el ID de AnyDesk o el alias del empleado, en my.anydesk II, vaya a la pestaña Clientes y elimine su cliente. Esto revoca su acceso a su libreta de direcciones.Restablecer la clave de licencia
Si tienen acceso a la clave de licencia actual, puede restablecerla en my.anydesk II > > de licencia Acerca > restablecimiento. Eliminar la clave de licencia de su cliente la degradará a una licencia gratuita.Restringir el acceso a clientes personalizados públicos
Si las direcciones URL públicas de cliente personalizadas se ven comprometidas, hágalas privadas o vuelva a crearlas para generar nuevos vínculos. Las copias ya instaladas no se verán afectadas, también debe eliminarlas manualmente de su licencia.Cambiar contraseñas de acceso desatendido
Actualice todas las contraseñas unattended access que se hayan compartido o guardado.Usar la lista de control de acceso (ACL)
La forma más eficaz de evitar el acceso es configurar la ACL en cada cliente para bloquear el ID o alias del antiguo empleado. Incluso si conocen sus contraseñas, no podrán conectarse si no están en la lista blanca.Aprovechar los espacios de nombres personalizados
Para facilitar la gestión, considere comprar un custom namespace. Las ACL admiten valores comodín, por lo que puede restringir el acceso a las sesiones que coincidan con*@yourcompanyname. Si quita la clave de licencia del cliente de un antiguo empleado, el alias con su espacio de nombres se elimina automáticamente, lo que impide que se conecte.